Introduction:
In the realm of carding, operational security is paramount. This guide will delve into the pitfalls that lead to the apprehension of carders. We will discuss the delicate equilibrium of trust within a perilous landscape, the frequently overlooked sphere of real-world operational security, and the lethal hazards of careless tool management. Furthermore, we shall explore methods of concealing one’s tracks and transitioning between online and offline activities.
1. The Allure of Swift Gains:
One of the gravest errors in carding is the prioritisation of rapid financial gain over robust security measures. This myopia manifests in numerous ways:
1.1. Overlooking Adequate Anonymity Protocols:
This is a prevalent error among novices. Many fail to consistently employ proper anonymity tools such as VPNs, VPS, RDP, or TOR, thereby exposing their genuine IP address. This digital signature can be tracked by law enforcement, leading them directly to your residence. The crux lies not merely in utilising these tools but in employing them correctly.
When engaging with carding shops and forums, TOR should be your principal ally. Opt for .onion sites wherever feasible and avoid logging into clearnet accounts. Frequently refresh your TOR circuits to evade establishing discernible patterns.
If utilising a VPN, select a no-logs provider situated outside the Five Eyes jurisdiction. Regularly alter your VPN server location to maintain an element of uncertainty. Activate the VPN kill switch feature to preclude accidental exposure in the event of a connection failure. Mullvad VPN is currently one of the most reliable VPN services available.
1.2. Neglecting Encryption:
This represents another perilous oversight. In the haste to execute transactions, some carders omit the use of PGP encryption for confidential communications. Should a marketplace be seized, unencrypted messages can prove invaluable to law enforcement. To circumvent this risk, apply PGP encryption to all sensitive communications, not solely those deemed critical. Regularly rotate your PGP keys to mitigate potential damage in the event of a compromise. Verify the PGP keys of your contacts to safeguard against impersonation attempts.
Contemplate employing encrypted platforms such as Session or Jabber for real-time communication, yet bear in mind that these are not infallible.
1.3. Reusing Identities:
This constitutes a frequent blunder that may precipitate your demise. The process of crafting new identities for each operation is time-consuming, but the reuse of a single online persona across multiple platforms establishes a traceable pattern. To mitigate this hazard, devise unique usernames, email addresses, and backstories for each platform you engage with.
Adopt diverse writing styles and vocabularies for each persona to elude linguistic analysis. Maintain meticulous records of your various identities, but ensure this information is stored securely and encrypted. Periodically discard outdated identities and generate new ones, even if the former have not been compromised.
1.4. Hastening Transactions:
This constitutes an unfortunate propensity stemming from the exhilaration of a substantial gain. Such haste can engender errors. Exercise patience and meticulously verify every detail prior to finalising a transaction. Avail yourself of escrow services when they are at your disposal to shield yourself from fraudsters and scammers, for instance, on the BCW forum, where escrow is available to facilitate secure purchases.
Interpose intervals between operations to regain composure and sustain concentration. The additional time invested in caution may preclude you from falling prey to a scammer or inadvertently revealing your activities to law enforcement.
1.5. Neglecting Operational Security Training:
This constitutes a pivotal error in an ever-evolving industry. The carding landscape is perpetually in flux, as are the methodologies employed to apprehend carders. Maintain a vanguard position by updating your knowledge on the latest operational security techniques. Conduct your own security audits to identify vulnerabilities within your operations. Devote time to mastering advanced techniques such as network traffic obfuscation and secure data destruction.
2. The Hazards of Overconfidence:
Triumph can engender complacency, and within the realm of carding, such complacency can prove fatal. Seasoned carders frequently succumb to this trap, believing they have mastered the game. However, the stark reality is that no one is impervious to risk. Let us examine how overconfidence can lead to the capture of a carder:
2.1. Omitting Crucial Steps:
This represents a perilous proclivity that may emerge after the successful execution of several operations. One may be tempted to bypass steps such as cleansing Bitcoins with Monero, executing Monero transactions, or performing DNS leak tests. This overconfidence can create substantial vulnerabilities in your security framework. It is a grave error to forgo Bitcoin mixing or Monero usage, as Bitcoin transactions leave an indelible trail on the blockchain, and law enforcement agencies are becoming increasingly adept at tracing these transactions. Always ensure that Bitcoins are cleansed or utilise Monero for augmented privacy.
Neglecting DNS leak tests is equally hazardous—a minor leak can divulge your genuine IP address. Conduct these tests prior to each session, without exception. Moreover, do not contemplate deactivating the VPN kill switch. Omitting to enable it can expose your genuine IP address should your VPN connection falter. It is not an optional feature; it is indispensable!
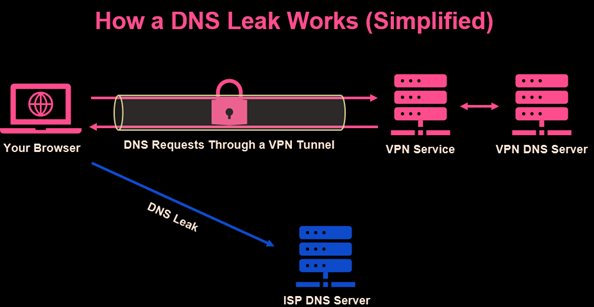
2.2. Disregarding Updates:
This represents another significant oversight. Neglecting to maintain your tools and knowledge in a state of contemporaneity can render you susceptible to novel detection methods employed by law enforcement. The tools and techniques of law enforcement evolve with remarkable celerity, and that iteration of the Tor browser from six months prior likely harbours vulnerabilities that have been rectified in more recent versions. Furthermore, law enforcement agencies are not averse to procuring zero-day exploits to compromise the security of widely-used privacy software. They are perpetually devising innovative strategies to apprehend carders, and they possess substantial financial resources to underpin their endeavours.
It is imperative to bear in mind that the tools upon which you depend for anonymity today may already be compromised, unbeknownst to you.

2.3. Rapid Expansion:
This is a prevalent issue among overconfident, successful carders. They may attempt to scale their operations at an accelerated pace, assuming more risk than they can prudently manage. This is the manner in which empires crumble. An increased volume of transactions correlates with a heightened likelihood of error. Can you sustain impeccable security while managing tenfold the volume? Hurriedly adopting new methodologies without thorough investigation can prove troublesome, as each approach possesses its own idiosyncrasies and potential pitfalls.
Incorporating new personnel introduces substantial risks. Can you place your trust in them? Have you subjected them to rigorous vetting? Do not forget that your security is only as robust as your most vulnerable component.
2.4. Compromising Personal OPSEC:
This represents a perilous consequence of success. It can engender laxity in your quotidian existence. Boasting about your “side venture” to family, friends or online is how rumours are initiated, and rumours can reach inopportune recipients. Abruptly procuring luxury items when your principal occupation does not support such expenditures is a red flag for investigators.
Your digital game may be secure, but what of your physical security? Are you meticulously destroying sensitive documents? Is your residential setup fortified against unanticipated visitors?
2.5. Underestimating Law Enforcement in 2025:
This is arguably the most perilous manifestation of overconfidence. Never forget that there are intelligent, dedicated individuals whose sole occupation is the apprehension of carders and hackers. That recently established, prominent forum may appear legitimate, but it could very well be a sophisticated sting operation.
Techniques that were effective last year may now be readily traceable, as law enforcement technology is in a state of perpetual advancement. Assuming safety because you are targeting another country? Reconsider. Law enforcement agencies are collaborating more than ever before.
3. The Peril of Misplaced Trust:
In the realm of carding, trust is a double-edged sword that can either fortify or undermine your operations. The anonymity inherent in this world is a breeding ground for deceit, and misplaced trust can lead to severe consequences, including incarceration.
3.1. Tools and Services:
Do you believe that the VPN you are utilising is impregnable, or that the cryptocurrency exchange you employ is genuinely anonymous? Think again. Not all services are created equal, and some will readily cooperate with legal authorities when pressured. Moreover, some of these services are honeypots, established by authorities to ensnare unsuspecting carders.
It is imperative to conduct thorough research on these services. Seek providers with a sterling reputation within the community, preferably those based in jurisdictions with robust privacy laws.
3.2. Close Associates:
In this enterprise, even those you hold dear can become your most significant vulnerability. That individual with whom you have collaborated for years may turn into an informant the moment they are apprehended and perceive an opportunity to safeguard their own interests. It is a harsh truth, but one you must acknowledge. Maintain a tight-knit circle, compartmentalise information, and always have a contingency plan in the event that a partner betrays you.
3.3. The Pitfalls of Indiscretion:
Online forums may serve as a valuable repository of intelligence but can also present opportunities for inadvertent revelations. It is alluring to disclose your triumphs or seek counsel, but excessive disclosure can create trails that guide authorities directly to you. Each morsel of information you divulge about your activities or private life furnishes investigators with pieces of a puzzle.
Bear in mind that the most prosperous carders are those who remain unnoticed.
Examples of forums seized:
https://www.cracked.io, https://www.nulled.to, BreachForums, RaidForums, among others.

3.4. Healthy Paranoia:
To endure in this world, one must approach every encounter with a judicious measure of doubt. Scrutinise every individual and entity meticulously. Foster trust gradually, if at all. And, above all, never divulge more intelligence than is absolutely necessary. In the sphere of illicit financial activities, the less others are privy to your affairs, the more secure you remain. Your apprehension is not merely warranted—it is vital for preserving your liberty.
4. Safeguarding Physical Operations:
Even with impeccable digital security, blunders in the tangible world can dismantle a carder’s entire enterprise. Recall that your virtual and corporeal existences are intertwined, and a single misstep in reality can nullify all your digital safeguards.
4.1. Unsecured Wi-Fi:
One of the most grievous errors is the utilisation of unprotected wireless networks. Connecting to public Wi-Fi without adequate safeguards is akin to publicising your actions to any eavesdropper. It is not merely a matter of convenience—that ostensibly “complimentary” café Wi-Fi could jeopardise your freedom.
Always employ a VPN when accessing public networks. However, do not cease there. Contemplate augmenting your defence with MAC address spoofing. This supplementary layer of protection can significantly enhance your ability to evade detection.
4.2. Reckless Crypto Transactions:
Another significant vulnerability stems from imprudent cryptocurrency dealings. You may believe you are being astute by employing digital currencies, but substantial or frequent exchanges from crypto to conventional money are akin to brandishing warning signals before financial entities. These institutions are perpetually vigilant for anomalous behaviour, and abrupt inflows of capital are prime targets for scrutiny.
You must devise a meticulous, forward-thinking strategy for liquidating your assets that does not attract undue attention. Focus on long-term sustainability rather than immediate gains.
4.3. Physical Security:
Inadequate physical safeguarding is an error even seasoned operatives may commit. Overlooking the security of tangible proof of your endeavours is akin to laying out a path for investigators to trace. Those scribbled notes containing card details, that storage device harbouring your illicit software, or those skimming devices concealed away? They all constitute evidence should authorities obtain a warrant. Secure storage, encryption, and possessing a robust obliteration strategy are indispensable components of your operation.
4.4. Ostentatious Expenditure:
Abruptly adopting a rock star “playboy” lifestyle when your ostensible occupation is menial? That will arouse suspicion, not merely from your envious acquaintances. Exercise prudence in this regard. Maintain discretion with your earnings. Possess a credible narrative to account for any elevated expenditure. Perhaps you engage in supplementary work as an independent programmer, or you have been prospering with digital asset investments. Whatever tale you concoct, ensure it withstands examination.
4.5. Online and Offline Lives:
Your virtual and tangible existences are interconnected, and you may not even be cognisant of this fact. That virtual private network you employ to obscure your internet activities will hold little significance if you are flaunting unexplained wealth or leaving incriminating evidence scattered about your residence.
Real-world operational security is not merely significant—it is absolutely vital to your enduring liberty and triumph in this endeavour. Do not permit a moment of negligence in the material world to nullify all your painstaking digital safeguards. Remain alert, maintain a healthy dose of scepticism, and perpetually consider how your online actions might translate into the tangible realm. Your freedom hinges upon it.
5. The Vulnerability of Tools:
In carding your tools are crucial but can also prove fatal if mishandled. It is a prevalent misconception that security tools are infallible, but the reality is that no instrument is flawless, and vulnerabilities are constantly being uncovered. Therefore, never become complacent with the tools you employ.
5.1. Obsolete Software:
One of the most grievous errors perpetrated by fraudsters is the use of antiquated software. Maintaining currency is essential for your protection. Cultivate the habit of verifying updates for all the tools you utilise and implement them promptly.
5.2. The Perils of Default Settings:
Another blunder is placing unwarranted trust in default settings. Merely because a tool arrives pre-configured does not imply that those settings are optimised for your requirements. Consider, for instance, the Tor browser. By default, it permits JavaScript, which can potentially disclose your actual IP address under specific circumstances. You must invest time in comprehending each tool you utilise and tailor it for optimal security, not merely ease of use.
5.3. Excessive Dependence on a Sole Instrument:
Placing disproportionate faith in a single tool or platform presents another susceptibility. Vesting all your confidence in one solution is akin to erecting your dwelling upon a solitary support. Should that support crumble, everything collapses. Diversify your protective measures and always maintain a contingency strategy. If one instrument falters or is compromised, you must be capable of transitioning to alternatives without endangering yourself.
5.4. Remaining Informed and Updated:
To ensure safety, you must keep abreast of the latest security intelligence and perpetually update your software, OS, etc. Contemplate utilising specialised operating systems such as Tails or Whonix for heightened protection.
6. The Hazard of Inadequate Obfuscation:
In carding, there is no such entity as excessive concealment. Many individuals engaged in this pursuit underestimate the significance of masking their trails, and this oversight leads to their undoing. You must recognise that a singular barrier is insufficient in today’s landscape.
Depending solely on one VPN or SOCKS is akin to placing all your valuables in a single, delicate container. You must consider multiple strata of protection, each contributing an additional obstacle between you and those attempting to monitor your actions. A Linux host OS with a VPN + Whonix (Tor) + RDP + SOCKS constitutes a four-tiered defence, making it exponentially more challenging for anyone to trace your activities back to you (theoretically, bearing in mind zero-day exploits and the fact that law enforcement possesses advanced knowledge and tools to track and monitor activities.)
6.1. The Risks of Metadata:
Another frequently overlooked facet of concealment is metadata. Those seemingly innocuous files and messages you transmit? They often contain concealed intelligence that may disclose more about you than you realise. Metadata can encompass the device model and OS version employed to generate a file, the precise moment and date of creation, the global positioning system coordinates of where a photograph was captured, or even your complete name as the document’s creator.
Always, meticulously remove metadata from any files you disseminate or upload. Employ ExifTool for images or metadata removal software for documents. For text-based communications, adhere to plain text format whenever feasible. It may appear to be a trivial detail, but it is precisely this type of detail that can unravel an otherwise robust operation. Keep in mind that investigators are trained to seek out these traces; do not provide them with a path to follow.
7. The Risks of Virtual-Real World Transactions:
7.1. Physical Goods:
One of the most significant dangers in carding arises where the digital realm intersects with the tangible world. These junctures are where the majority of individuals engaged in this pursuit are apprehended. Consider, for example, the logistics of shipping and intermediary locations. Transporting physical items from one location to another generates a documentary record that can be traced back to you.
To mitigate this peril, you must employ multi-stage shipping and scrutinise your intermediary addresses. Never utilise the same location for substantial acquisitions, and always possess a plausible explanation for receiving parcels at that site.
7.2. Cash-Out Procedures:
Cash out transactions present another substantial vulnerability. Transmuting your digital earnings into tangible currency is where most fraudsters are detected. Financial institutions possess advanced mechanisms to identify money laundering and are perpetually on heightened alert. Substantial inflows, recurrent modest inflows just beneath reporting limits, abrupt shifts in account behaviour, and dealings with high-risk nations are all prominent indicators of illicit activity. Even ostensibly innocuous actions, such as depositing round figures, can arouse doubt.
You must devise a meticulous liquidation strategy that avoids triggering these alerts. This may involve distributing your liquidations over an extended duration, varying transaction magnitudes, or employing multiple techniques and accounts to convert your digital assets into conventional currency. Recall that banks are legally obligated to report dubious behaviour, so maintaining a low profile is crucial for the enduring security of your enterprise.
7.3. Direct Meetings:
Confrontations with fellow fraudsters or purchasers pose very high hazards and should be evaded whenever feasible. The anonymity that shields you in the digital sphere vanishes the instant you enter the tangible realm.
7.4. Prudent Device Management:
Managing your equipment is another crucial element of digital-material transitions. Your tangible apparatus can connect your internet endeavours to your authentic persona if you are not vigilant. Employ designated instruments for illicit activities and never intermingle them with personal use. This entails distinct telephones, distinct computers, and ideally distinct internet connections. When these instruments are not in use, ensure they are securely stored and encrypted.
Conclusion:
Carding demand unceasing vigilance, ongoing education, and meticulous attention to particulars. The hazards delineated in this guide have felled numerous individuals engaged in this pursuit, from novices to veterans. A single misstep can be catastrophic.
Bear in mind that absolute security is a myth; there are only varying levels of jeopardy. Each action you undertake should be evaluated in terms of potential exposure. Authorities are not trifling; they are well-resourced and intensely motivated. Never underestimate the capabilities and resolve of those who seek to apprehend you.
The world of carding is in a state of perpetual flux, as are the techniques employed to identify and capture carders. Prioritise remaining informed and current with the latest methodologies and safety risks.

