How to Become a Pro Hacker
The hacking you know today started in the 1970s when Dennis Ritchie invented the “C” programming language. However, the term originated at the Massachusetts Institute of Technology, a private research university in Cambridge, Massachusetts, in the 1960s.
I understand that becoming a hacker is tough, but every elite hacker today started somewhere. At some point, you would feel like giving up. The point you feel like giving up is the point where you’re about to get into a new level of hacking.
Introduction to Hacking
I picked interest in how to become a hacker In the early 2000s, and all it took me was 15 minutes. After a year of scripting, programming, and thinking, I walked out of the white hat hacking industry. It was quite frustrating, and this happened because I couldn’t bypass a particular task. Three months later, I returned, why back to the job, and conquered. Do you want to know what role? Never mind until you get there.
Who is a Hacker
Generally, a hacker masters the art of programming and solving technical problems using a computer, his brain, and other mechanical devices.
We have six major types of hackers. They include a white hat, black hat, grey hat, hacktivist, cracker, and scripter.
White Hat Hacker
He/she is all about ethics and not about unauthorized access. I picked interest in this, and it’s quite cool. A white-hat hacker is also called an ethical hacker. This category is for those interested in how to become an ethical hacker for money.
Black Hat Hacker
This is the opposite is white hat and deals with unauthorized access to whatever is the target; internet, software, etc.
Grey Hat Hacker
A grey hat hacker is a black hat hacker. However, he/she reveals the vulnerabilities present in an organization’s system.
Hacktivist
Most of the movies you find featuring hackers fall under this category of hackers. A hacktivist can be a black or white-hat hacker. The aim of this hacking class is usually to draw attention to political reasons. Practically, these hackers are being hired, especially during political seasons. If you are interested in how to become a hacker for the government, this is your category.
Cracker
Crackers are the noisiest of all. They consider themselves hackers but are not. These are the set of self-acclaimed hackers you’ll find cracking video games for coins, rewriting software, etc.
Scripter
A hacker of the class is not a core hacker. They are not regarded as hackers. They use ready-made tools to run their activities, and the results are not always 100%. They often pay for the tools and expose their secrets to the developers they buy these tools from.
Note: Hacking can be a group or individual affair. For beginners, I recommend starting as a group to learn quicker.
What is Hacking
Everyone thinks hacking is all about breaking into a networking system because of what they see in the movies. You think so
? The truth is that a hacker does not just deal with finding network vulnerabilities to breach.
Hacking extends to information tracking and internet breaching. Hacking is all about finding information and building on the news. Having equally involves cutting into servers and retrieving things that are not meant to be known.
Hacking could be targeted at P2P networks, an organization’s database, websites, etc.
Hey, when people talk about teaching you how to become a hacker in 15 minutes, run! That isn’t hacking, but cracking, which would involve the use of ready-made tools.
In this article, I’m exposing the basics of how to become a hacker for the government. You’ll also figure out that knowing how to become a computer genius/hacker requires determination.
How to Become a Hacker – Basics of Ethical Hacking
- Pick a Hacking Niche
You should understand the type of hacker you want to become. I mentioned six kinds of hackers. Each of these hackers makes good money in the long run with hard work. Of all the categories, ethical hackers are believed to be the richest. It is unclear how rich black hats hackers are, but it is their connections that give them the riches. Just so you are aware, they also risk jail terms, though.
Do you want to become the type of hacker that wows your friends? Spies on a girlfriend? Or, are you about erecting a hacking career and making money from hacking?
Moreover, understand that each niche has its requirements, and you must meet up the requirements to be successful.
- Understand the Deeper Functions of a Computer
Concerning how to become a hacker, you need a broad knowledge of the computer. A computer is more than what people use for movies, video calls, texting, gaming, video editing, graphics design, etc. It embodies millions of functions, such that the manufacturers never inform you.
The only way to access these features is through the use of third-party software or inbuilt software.
Also, understand the basics of networking in computers. Look out for abbreviations like DNS, DHCP, IPv4, IPv6, VLANS, NAT, ARP, etc.
Finally, learn how to interact and instruct the computer using the command prompt. If you can modify the registry without breaking the system, then you’re OK to proceed.
- Learn How to Code
You can’t become a hacker without coding. So, if you’ve yet to learn to code, it’s needless to be here. Maybe your interest is on how to become a hacker in 15 minutes. Unless this is the case, you must know how to code.
You do find people who claim they can teach you how to hack without coding. That’s quite true, but does that make you a hacker? Besides, you would be exposing your ideas to those people, and they’ll use that to develop their hacking abilities.
For example, I find people flooding a website that reads something like “Hack a Facebook Account by Inputting Username Here.” You think they’ll get back to you with a response like “here is the hacked account”? They will never, and even if they could breach that account, they will not share it with you.
Learn to code, understand the ethics, and code something out for yourself. There are several ways to hack a Facebook account, for instance. If you’re using the SS7 attack or credential harvester like Kali Linux, you require the knowledge of coding.
- Select a Programming Language
There are a couple of programming languages out there. You should pick and familiarize yourself with a Programming Language. I started with C programming language, and it’s recommendable. It is what hackers widely use, except for those that want to advance. It’s a fast assembly language that could be used to hack virtually anything. What I also like about the C programming language is the fact that UNIX is written in the C language. You may as well opt for C++.
I will categorize hacking in this guide into a database and networking. Let’s talk about these two aspects of hacking.
Building Your Database Skills
Like I stated earlier, coding is the basis of hacking. If you’re freaking about database hacking, you may opt for PHP, Java, Python, SQL, UNIX, etc.
Let me introduce you to the above mentioned coding language.
PHP
PHP is quite cool if you’re dealing with connecting forms or webpages to the database. Before you drive into PHP, you should understand CSS, HTML, and JavaScript. The most important of all is HTML since we are dealing with the internet. With PHP, you are heading towards becoming a full-time data retriever and a black hat hacker.
Combining PHP knowledge with MySQL favors you to tweak the database anyhow you want.
Java Script
You can become a hacker without JavaScript, but you still require it. For sure, some instances will require knowledge of JavaScript to bypass. It would help if you also had a good understanding of HTML to be great.
JavaScript allows you to steal data online. With this programming knowledge, you can track targets and obtain the data you require for whatever over the web. Also, it’ll be easy for you to crack application software for whatever purpose.
Python
Python is an easy-to-learn language. It is most recommended for a beginner and can easily retrieve information from the database without authorization.
MySQL or SQL
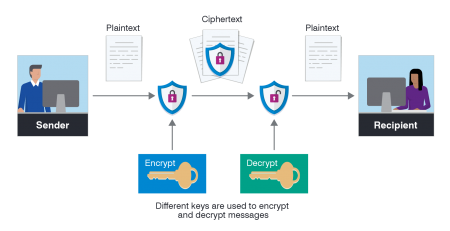
People believe in encryption information on the database. However, with MySQL or SQL, a hacker can easily decrypt and retrieve this information. You can go on to modify the data and key in whatever you want you. You may even install destructive codes that can take down the database and cover your way out after the deed. If you want to know how to become a hacker for the government, you need to perfect your hacking skills.
UNIX
UNIX is written in C, just like PHP. Understanding how UNIX operates means you’re in the hacking world because it is based on commands.
While I was using Windows 7 and Max OS, I thought I knew everything until I installed a UNIX operating system. A newbie wouldn’t know a thing about Linux because of its complexity.
Other than Kali Linux, which I used, there are other ones like Ubuntu, Fedora, Parrot, Linux Mint, BackBox, etc. With any of these OS, you’ll be able to run the UNIX program.
If you refer to UNIX using Microsoft Windows or Mac OS, understand that you’re wasting your time. The Mac OS is even better because it will not limit you like Microsoft.
If you’re ready to be stressed and frustrated, begin with Kali Linux like myself. If you need something less frustrating, opt for Ubuntu. Still, I can’t guarantee that it will be less frustrating.
- Write HTML Using WWW
When you visit www.smartlazyhustler.com, the pictures, text, and every other thing you find are made possible with HTML coding. If you want to confirm, launch the browser on your computer. Open www.smartlazyhustler.com and right-click. Select the inspect page element if you’re using Firefox. You should find a collection of HTML codes right there. You may not understand what they mean unless you know what HTML is all about.
Do a little web search and try to do some operations on your own. It isn’t difficult if you’re determined, though.
- Interested in Cryptography?
When you arrive at this stage, you’re almost making yourself a hacking lord. As a beginner, forget about this stage of hacking until you’re good at the ones above. For now, I won’t say much about this. But, if you can integrate this at the early stages of your learning, it isn’t a bad idea.
Steps Towards Becoming an Elite Hacker
Employ Creativity
Employing creativity is all about being real and inventing what is not already there. I started by building a virus as well as building an antivirus that can take down the virus. There are several other things to pick and work on and make it big. You could make an app that steals identity and try it out on your friends.
Stay Focused
To become an ethical hacker, you must be focused. The understanding of hacking doesn’t just lie in writing the codes. It can be very frustrating for a beginner, especially after hours of hard work; bugs wouldn’t allow you to succeed.
Don’t Walk Out On a Problem
I walked out on a problem once, but I returned a few months after. It would have been silly if I didn’t go back. I conquered the challenge and became even better.
There are times you’d feel like smashing your personal computer. It’ll feel like it’s a waste of time, whereas it isn’t. Take a break rather than walk away. Sometimes, your brain has is overloaded, and it requires rest to refresh.
Check Hacking Forums
Sign up for top hacker forums like HackerForum or any other. There are dark web forums that deal with the most mysterious aspects of hacking. I know you would love to be there, and I would love you too. For some reason, I will not post the links here. Moreover, you require secured networks like Tor to access them.
Forget about Google, Bing, Yahoo, etc. They can never direct you there. Maybe DuckDuckGo can, but with ordinary browsers.
Refer to Online Resources
Some resources are paid while others are free. Pick anyone to boost your learning process. Besides, some paid hacking guides are free on dark web hacking forums.
Stay Ghost
Oh yes, don’t be a noisy hacking student. The worse of all is that you may attract the Feds to start nosing around your neighborhood. Keep everything to yourself, and always cover your rear and front cameras while surfing the web. One more thing, be careful while on the dark internet. I’ve been there; it’s messy, although it looks like nothing is going on there.
How to Help and Learn from the Hacking Community
Test and Debug Open Source Applications
Once in a while, software developers request for users to test their products before release. Companies like Google often do this with their software to know where to revise and all of that. Take chances and see what you can do with such products. Do not attempt this with closed source software. If you’re, however, tempted to do so, do not redistribute such software.
Publish Hacker Articles
My skills improved as a result of this. When you publish the little, you know, you’ll attract pros who’ll flood in to make corrections or advise you on your flaws. Some do be harsh when correcting you. As such, do not write like you’re a genius. Also, state that you’re open to corrections at the end of each write-up.
Share Your Hacking Experiences
This could be done by commenting on forums and answering questions in areas that you understand.
Are you interested in hacking? Let me know in the comment sections.
Ultimately, when you eventually become a successful hacker, you can use the skill to collect bank account details and play around with loved ones.










Comments (7)
wow
There is a software am hearing now but I don’t know if it is working or fake cardro pro app
I’m very interested, sir please help me out
Hello boss please can you teach me how to make money, am just tired in this life with the sufferings,, pls boss, thanks as I hear from you,,
thanks for this article,am ur biggest fan
hey cashout..thnks i follow u everyday,please tell me how to make money
I’m need to all of this but interested on learning how to do logs and fullz can you please tell me where to start