LATEST METHOD AND STEPS ON HOW TO STAY INVISIBLE AND ANONYMOUS ONLINE
In this 2022 Cashoutgod guide we will explain how you can stay anonymous to ensure your privacy and (more importantly) freedom.
As part of this check, first you are going to set a trap, yes that’s right! This trap will ensure if someone else is reading your correspondence (suitable for email, instant messengers, social networks, websites and forums, SMS and so on).
Here we will show you how you can check if you’re being monitored and spied upon whether it be via mail or social networks.
We used this method on a popular social network, creating a provocative personal message that the content moderation teams should be able to read.
Once they’ve read your message(s), and you see that our messages are being read. Perhaps you want to check if your spouse, hacker or boss is reading your correspondence – this method is perfect for you.
PRIVNOTE
The essence of the proposed method is to create a hook link that will be added to the message. The trap will be created using a one-time Privnote.
The beauty of “Privnote” based messages is that after reading the message self-destruct itself, yes, it gets deleted, and it is impossible to resurrect that message back in order to read it – this functionality of the service is known to many, but not everyone knows that Privnote has the ability to receive a notice of reading the note by email.
The first thing you need to do is create a Privnote.
Be sure to select the option “Do not ask for confirmation before showing and destroying the note (as in Privnote Classic)” when creating a note, we do not need any confirmation.
Be sure to indicate “E-mail for notification of the destruction of the note.” It is necessary to receive a notification as soon as the note is read. After creating a note, you get a link like:
- “https://privnote.com/aKNEmQHl#DcieTk7Gz.”
We will not send a link to Privnote, we will change it, for example, through the Bitly short link service. The link will look something like this:
- “https://bit.ly/2JFYEGV.”
Then you send the recipient a message containing this link by email, messenger or social network. It is desirable to design the message so that the attacker would be tempted to follow the link. For example, like this:
- “All documents on the upcoming transaction.”
The real recipient must be notified ahead of time that this message is a “decoy” so that he/she will NOT open the link and the trap will work for the person who is spying on you. The original recipient should not click on the link, but instead the secret/spy reader of your correspondence will click on it.
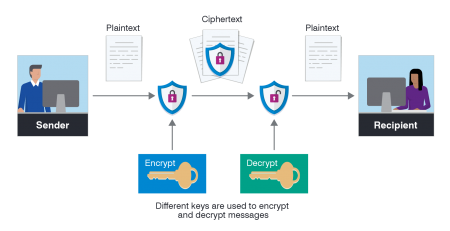
The correspondence can be referred to as the “person in the middle”, for example, by a moderator of a social network. In this case, you should change the communication method or encrypt the transmitted data.
It is much more dangerous if the correspondence is read on the device of the sender or recipient. We recommend placing traps on devices and checking if someone else has access to them.
SOFTPERFECT WIFI GUARD
Now let’s look at unauthorized use of your WIFI. It can be your neighbor who thinks he/she is better at penetrating your security or simply an intruder; So as part of the test, we will scan your Wi-Fi network and find all connected devices, as well as set up a notification system for unauthorized connections to your router.
Checking the Wi-Fi network for the presence of third-party connections In this test, we will scan our Wi-Fi network and check for the presence of third-party connections in it. For example, in this way you can find out if a neighbor or an intruder is connecting to your Wi-Fi, and indeed you can see all connected users. For this test, we need SoftPerfect WiFi Guard.
The “SoftPerfect WiFi Guard” program scans the network and shows the user a list of currently connected devices, displaying available information about them, such as the MAC address, manufacturer and internal IP address (the latter, however, is interesting only for specialists).
SoftPerfect WiFi Guard can also work in passive monitoring mode, scanning the selected network at a specified interval, and if unknown devices are found, notify the user about this using a pop-up window.
In other words, if a neighbor/intruder suddenly connects to your WIFI, the program will detect it and notify you.
SoftPerfect WiFi Guard is available on Windows, macOS and Linux devices.
The free version of the program limits the output of information to five devices: if you have five or fewer devices connected to your WIFI, the free version is enough for you, if more, you will have to pay a one-off fee for a license… we are not associated with SoftPerfect WIFI guard financially or any other way), in a vast majority of cases you can use the free version to get the job done.
Using SoftPerfect WiFi Guard on Windows, Linux and macOS The program works roughly the same on all devices, so we’ll show it using macOS as an example.
After reading the instructions, you can easily run the program on Windows or Linux. Download and install SoftPerfect WiFi Guard to get started. When you start WiFi Guard, you will be immediately prompted to configure the program. The main thing here is to choose a Wi-Fi network adapter.
Let’s move on to scanning the network. Do not be alarmed if the system detects unknown devices on your network during the first scan. For the program, all devices are now unknown, except for your computer from which the scan was launched. The unknown devices found are likely your phones, tablets, or your family members’ devices.
How can you check this?
By MAC Address: By comparing the MAC addresses of the discovered devices with the MAC addresses of your devices.
To find out the MAC address of your device, read this chapter. If all found devices are yours, we recommend adding them to the whitelist so that the program does not mark these devices as unknown in the future and does not raise an alarm when they are detected.
Select the device that you know by double-clicking on its name with the mouse. In the form that opens, select “I know this computer or device.” The selected device will be added to the whitelist.
The program will continue to scan the network and if it detects unfamiliar devices, it will immediately notify you about them. We recommend that you run a scan periodically, for example, once a day, but whether to conduct a constant regular scan is already your choice. For security, this is certainly a big plus, since with a regular manual check, there is a possibility that the attacker will not be connected to the network at the time of scanning.
There is another interesting indicator – “Ping”.
It will help to find out how long the signal takes from the investigated router to the detected device and, accordingly, how far from the router it is located.
First of all, determine the ping to the router from the device from which the scan is carried out, let’s assume it is 9ms.
The ping from your computer to the unknown device is 19ms, from there you subtract the ping to the router, and 10ms remains, which means that the device under investigation is approximately the same distance from the Wi-Fi router as your laptop from which the scan was conducted.
What if you find unknown devices on your network?
So, you ran a test and found unknown devices on your WIFI network. This is an alarm bell, and you urgently need to take care of the security of your Wi-Fi router.
Here we will write a short list of measures, they will be discussed in detail within the framework of this chapter on configuring the security of a WiFi router. Add attackers’ MAC addresses to the blacklist of the router by conduct a security audit of the router.
You should change passwords: for both administrator and network connection. If you want to scan the traffic of the uninvited guest and see for what purposes he uses your router. Set SoftPerfect WiFi Guard to scan regularly for at least a 4 to 6 weeks to make sure the problem is resolved.
Does your password contain both upper and lower case letters?
If not, then you should. Modern practice recommends using letters of different registry, numbers and password length should not be less than 8 characters.
Alternatively, we can recommend that you use foreign language letters in your passwords – this way you can save the old password, you just need to change the keyboard layout (amazing isn’t it?).
You can also check our personal data for “use” or “on sale” on the “surface net”.
The proposed methods will allow you to check whether intruders are using your personal data, such as copies of documents, photographs, for illegal purposes or whether they are being sold on the black markets
How to check if your data has already leaked into the hands of cyber-rebels (cybercriminals)? Disclaimer: We do not know of guaranteed verification methods that can give an accurate answer about the presence or absence of your personal data from cyber-rebels as mentioned above.
LEAKS (who farted?)
You can check the availability of your accounts in publicly known databases leaked to the network using this link.
Data leakage is not always accompanied by identity theft, for example, access to email may not be enough to steal an identity if no information is there.
Even stealing an account on a social network if there is no genuine information there should not be considered identity theft.
However, your accounts can be used for illegal purposes, which we discuss below, and this can lead to the consequences of more terrible identity theft.
A lot of personal data ends up in the hands of hackers, special services, or even in the public domain due to leaks from hacked websites databases.
You need to be aware of the news of leaks, and if your personal data was on the compromised site, you will at least be aware that now this data is in the hands of the “bad guys”.
We cover how to monitor for leaks in detail in the chapter on data leaks. Of course, this method does not provide guarantees, since the leak may not be recognized or the news will not appear on the proposed sites.
Sometimes it becomes known about leaks too late, as in the case of Yahoo users, who found out only a few years later that all email inboxes were compromised (except for compromise, it became known that the US intelligence services had access to mail and analyzed letters for words- beacons).
Search by photos; Check your photos that you have posted publicly for use on third-party resources or social media accounts. We tell you in detail how to do this in the chapter “What can be found out from a photograph”.
Search by first and last name; This advice only works if you have a rare first and last name. Many services allow indexing of user accounts, and you will immediately find out that there is a registration using your data, but again in the case of a rare combination of first and last name.
Contacting the vendors of stolen data; They can be found through a search, for example, by the request “buy photocopies/scans of a passport”, “buy a photo of documents”, they can also be found on the Darknet markets such as “ManCave”.
From communication with such sellers, our understanding is that many of the documents are sorted, and they can make a fairly accurate sample up to the date of birth.
This is what we use for verification. You choose a certain amount of information about yourself, for example: “woman, 1978, registration California, birthday in July, traditional unremarkable first and last name.”
Next, you write to the sellers that you will pay “a bit more” for copies of user documents with similar data. Offer a really good amount to motivate them to look well .
If the seller reports a suitable kit or kits are available, ask for proof before paying. For example, copies of documents in poor quality,with shaded data and other other means of protection (watermark) since you already recognize a copy of your document.
These are all methods we know so far. In the next chapter, we will tell you what to do if your identity is stolen.
We check our email for resistance to hacking from hackers. In this test, you will order hackers to hack your own mail.
Here we are talking mainly about email, but the proposed verification method can be applied to both social media accounts and messenger accounts.
For most users, email is tied to various services, and hacking email allows an attacker to gain access to them. If you are serious about the security of your data, most likely you are using this recommendation, and hacking your mail will not lead to hacking accounts associated with email as long as you have set different passwords.
However, you must admit that it is not pleasant if someone gets access to the contents of your mail. At one time, hacking personal mail cost Hillary Clinton the post of President of the United States.
Let’s simulate a situation when your ill-wisher, for example a business competitor, orders a hack of your mail, and we will order it ourselves.
This will be an excellent test of account protection, so to speak, a proactive action. The first step is to find a hacker or a service that provides services to hack mail accounts.
To do this, you do not have to go to the Deep/Dark Web, you can contact us and ask for assistance or else google “hacking email”, and you will be offered a lot of services dealing with hacking mail.
But be very careful, some of them might not be the actual hackers, yes they might be scammers who set themselves the sole purpose of getting money from you.
They will also ask for an advance payment, you can politely move onto next as your aim is to get someone who works for you with “no up front payment” AKA “for free”,
But scamming even gets darker there are scammers. Some time after ordering, such a scammer will report that the victim’s mail has been successfully hacked and for confirmation he sent you a letter from the hacked mailbox through his program.
But since the sending went through the program, the letter most likely ended up in spam. Of course, after that the “hacker” will ask for money for the work.
Remember, there is no program, as well as hacking mail, in this case, a banal substitution of the address is used, and such letters are immediately sent by mail services to spam.
Extortionists can also get caught, who, having received an order, will begin to blackmail you. The essence of their proposal usually boils down to the following: either you pay money, or they transfer all information about your order to the victim and / or to law enforcement agencies.
As you can imagine, in our case it is not scary. Among the scammers and ransomware are real services that start checking your email inbox for resistance to various hacking methods.
TOR (THE ONION ROUTER)
The first reaction to the news about PRISM was the same for many: We will NOT allow ourselves to be monitored, we will install Tor.
This is, perhaps, in fact the most popular tool, which we have talked about more than once on the pages of our magazine. It was also created by the American military, albeit for completely opposite purposes.
Users run the Tor software on their machine, which acts as a proxy, it “negotiates” with other network nodes and builds a chain through which encrypted traffic will be transmitted.
After some time, the chain is rebuilt and other nodes are used in it. To hide information about the browser and the installed OS from prying eyes, Tor is often used in conjunction with Privoxy, a non-caching proxy that modifies HTTP headers and web data. allowing you to maintain privacy and get rid of annoying ads.
In order not to crawl through the configuration files and edit all settings with handles, there is a wonderful GUI shell – Vidalia, available for all operating systems and allowing you to open the door to the anonymous world on your PC in a couple of minutes.
The developers tried to simplify everything as much as possible, allowing users to install Tor, Vidalia and a portable version of Firefox with various security addons in one click. For secure communication, there is a decentralized anonymous messaging system – TorChat.
The Tortilla utility is used to safely, anonymously and transparently redirect all TCP / IP and DNS traffic through the Tor anonymizer network. The program allows you to anonymously run any software on a Windows computer, even if it does not support SOCKS or HTTP proxy, which was almost impossible to do on Windows before.
In addition, for the standard bundle Tor + Vidalia + Privoxy, there is a worthy alternative – Advanced Onion Router https://sourceforge.net/projects/advtor/, a portable onion routing client. For those who are especially concerned about their security, there is a Live CD distribution that is configured out of the box to send all traffic through Tor https://tails.boum.org/
The main purpose of Tor is anonymous surfing plus the ability to create anonymous services. True, anonymity comes at the price of speed.
TOR VIDALIA
In addition to onion routing, there is also garlic routing used in I2P. Tor and I2P, with some external similarities, largely implement diametrically opposed approaches.
In Tor, a chain of nodes is created through which traffic is transmitted and received, while in I2P “inbound” and “outbound” tunnels are used, and thus requests and responses go through different nodes.
These tunnels are rebuilt every ten minutes. “Garlic routing” means that a message (“garlic”) can contain many “cloves” – fully formed messages with information on their delivery. In one “garlic” at the time of its formation, many “cloves” can be laid, some of them can be ours, and some of them are transitory.
Is this or that “clove” in the “garlic” our message, or is it someone else’s transit message that passes through us?
The main task of I2P, unlike Tor, is anonymous hosting of services, and not providing anonymous access to the global network, that is, hosting websites on the network, which in I2P terminology are called eepsites.
Java must be pre-installed for the I2P software to work. All management is carried out through the web interface, which is available at 127.0.0.1:7657.
After all the necessary adjustments, you need to wait a couple of minutes until the network is configured and you can use all of its hidden services.
In this case, we got anonymous access to the I2P network, that is, to all resources in the .i2p domain. If you want to go to the global network, then you just need to register the use of a proxy server in the browser settings 127.0.0.1:4444.
The exit from I2P to the WAN is done through specific gateways (called outproxy). As you understand, in this case, one cannot count on great speed. Plus, there is no guarantee that no one will sniff your traffic on such a gateway.
Is it safe to host your anonymous resource on an I2P network?
Well, no one can give a 100% guarantee of safety here, if the resource is corny vulnerable, then it will not be difficult to determine its true location.
OBFS PROXY
In many countries, such as China, Iran, providers are actively fighting against the use of Tor, using DPI (deep packet inspection), keyword filtering, selective blocking and other methods.
In order to bypass censorship, torproject has released a special tool obfsproxy https://2019.www.torproject.org/docs/pluggable-transports, which converts traffic between the client and the bridge in such a way that it looks absolutely harmless to the provider.
GNU NET
What about secure and anonymous file sharing? For this purpose, you can use GNUnet https://gnunet.org/en/
A framework for organizing a secure P2P network that does not require centralized or any other “trusted” services.
The main goal of the project is to create a reliable, decentralized and anonymous information exchange system. All nodes on the network act as routers, encrypt connections to other nodes, and maintain a constant load on the network.
As with many other solutions, nodes actively participating in the network are served with a higher priority.
To identify objects and services, a URI is used, which looks like gnunet://module/identifier, where module is the name of the network module, and identifier- a unique hash that identifies the object itself.
An interesting feature is the ability to adjust the level of anonymity: from zero (not anonymously) to infinity (the default is one). For secure transmission, all files are encrypted using ECRS (An Encoding for Censorship-Resistant Sharing).
GNUnet is extensible and can be used to build new P2P applications. In addition to file sharing (the most popular service), there are alternative services: the simplest chat, which is now in a half-dead state, as well as a distributed DNS.
Well, as usual, you have to pay for anonymity: high latency, low speed and a fairly high consumption of resources (which is typical for all decentralized networks).
RESTRO SHARE
RestroShare https://retroshare.cc/index.html is an open cross-platform program for building a decentralized network based on the F2F (Friend To Friend) principle using GPG.
The basic philosophy is to share files and only communicate with trusted friends and not with the entire network, which is why it is often referred to as a darknet.
To establish a connection with a friend, the user needs to generate a pair of GPG keys using RetroShare (or select an existing one). After authentication and exchange of the asymmetric key, an SSH connection is established using OpenSSL for encryption.
Friends of friends can see each other (if users have enabled this feature), but cannot connect. Such is the social network

. But you can fumble folders between friends. There are several communication services on the network: private chat, mail, forums (as anonymous,
RASPBERRY Pi
You might be wondering: what does the Raspberry Pi have to do with it?
We’re talking about anonymity. And despite the fact that this little device will help achieve this anonymity. It can be used as a router / client giving you access to Tor / I2P networks or anonymous VPN.
Besides this, there is one more plus. In decentralized networks, it is possible to achieve an acceptable speed of access to intranet resources only if you are constantly in it. For example, in I2P, the trust of other “garlic routers” to such a node will be greater, respectively, and the speed will be higher.
It is unreasonable to keep your computer on all the time or to start a separate server for this, but it seems that it is not a pity to spend only $30 on it. In everyday life, you can use the usual connection, and when you need to go online anonymously, you just let all the traffic through the mini-device and don’t bother with any settings.
We must say that until recently there was no point in installing the I2P software written in Java on the “blackberry”. The resource-hungry Java machine lacked the standard 256MB of RAM.
With the release of the Raspberry Pi model B, which already carries 512MB on board, this has already become quite real. So let’s take a look at the basics related to installation. Let’s say we use So let’s take a look at the basics related to installation. Let’s say we use Raspbian. First of all, we update:
Code:
sudo apt-get update; sudo apt-get dist-upgradeThen we install Java, but not the standard package, but a special version tailored for ARM processors – https://wiki.openjdk.java.net/display/OpenJFX/OpenJFX+on+the+Raspberry+Pi (as practice shows, the standard version will gobble up all the memory). Download and install:
Code:
sudo tar zxvf jdk-8-ea-b97-linux-arm-vfp-hflt-03_jul_2013.tar.gz -C / usr / local / java
export PATH = $ PATH: / usr / local / java / binThen download and install I2P:
Code:
cd ~
mkdir i2pbin
cd i2pbin
wget http://mirror.i2p2.de/i2pinstall_0.9.7.jar
java -jar i2pinstall_0.9.7.jar -consoleTo turn Raspberry into a router for I2P, you need to do a little bit of configs. Go to ~/.i2pand start editing the file clients.config. There we need to comment out the line
Code:
clientApp.0.args = 7657 :: 1,127.0.0.1 ./webapps/and uncomment
Code:
clientApp.0.args = 7657 0.0.0.0 ./webapps/And then in the file, i2ptunnel.configreplace the addresses in the lines
Code:
tunnel.0.interface = 127.0.0.1
tunnel.6.interface = 127.0.0.1on 0.0.0.0. Then we can start the I2P router by running:
Code:
cd ~ / i2pbin
./runplain.shYou can also add the following lines to the crontab so that the software automatically rises at system startup or after a crash:
Code:
0 * * * * /home/pi/i2pbin/runplain.sh
@reboot /home/pi/i2pbin/runplain.shIt remains only to organize remote access to the device. The best way is to use dynamic port forwarding over SSH.
To do this, you just need to set the I2P tunnel in the settings, which would point to the 22nd port on the local machine. In the same way, you can turn Pi into an anonymous VPN (how to do this, you can see here – https://lifehacker.com/turn-a-raspberry-pi-into-a-personal-vpn-for-secure-brow-5978098 or connect to Tor (an excellent video tutorial about this here https://blog.adafruit.com/2013/07/19/raspberry_pi-piday-raspberrypi-5/ or you can come up with your own way of how to use the device for anonymous travel on the Web.
MIKROTIK
In fact, the Raspberry Pi is not the only small device on the basis of which you can organize anonymous Internet access.
A worthy alternative to it will be a router from the Latvian company MikroTik, which produces network equipment and software for it. Such a device will cost a little more, but it will require less fiddling when setting up.
RouterOS products include a Linux-based operating system designed for installation on MikroTik RouterBOARD hardware routers. Different options for the RouterBOARD platforms allow you to solve various network problems: from building a simple access point to a powerful router. Despite the presence of a power connector, almost all devices can be powered using PoE.
A big plus is the availability of good documentation, for those who want to check it out gere is the link https://wiki.mikrotik.com/wiki/Main_Page, which describes in great detail how you can create a security router based on RouterBOARD4xx by connecting it to the Tor network.
BROWSER ADD ONS
Most of the time on the Web is not spent on Skype conversations or chatting on social networks, but on simple surfing. But even here we are not left unattended. Social networks and other sites are trying to track what resources you visit, what you are looking for on the Web, in order to then stuff you with ads on similar topics (as soon as I looked at one laptop, it immediately started popping up everywhere in Google ads).
This quickly becomes annoying and distracting from the main search. Anyway, we do not go to the Internet in order to show someone what we are looking for. So we have to deal with this somehow.
DISCONNECT
One of the best ad-tracking plugins available for Firefox, Chrome, Opera and Safari browsers.
On the official website, you can watch a funny animation showing how some sites follow users and prevent them from focusing on search.
After installing this extension, a button will appear on the toolbar, upon clicking on which a drop-down window (dropdown) will be displayed, and it will clearly show how many “left” requests (from Google, Twitter, Facebook, analytical and advertising sites) were blocked when entering this page. And also how much the page load time was reduced and how much traffic was saved.
ADBLOCK PLUS
Another way to track the user (and often the distribution of malware) is through advertising. And even though most of the banners are quite harmless, you must admit that a bunch of animations and pop-up pop-ups are not only annoying, but also distract attention from the information you are looking for.
To disable ads in Firefox, Opera and Chrome, just install the Adblock Plus extension.
DONOTTRACKME
An alternative to the popular Disconnect, which also supports all popular browsers, is DoNotTrackMe.
The interface for both extensions is very similar. However, unlike a more advanced competitor, DoNotTrackMe gives the user the choice to block a particular spy site.
This approach is useful for those who want to leave everything as it is, blocking only a few violators.
GHOSTERY
Another extension that allows you to block resources trying to track your location on the Web.
Has a large database of “spying” sites. Unlike colleagues in the shop, it supports IE. Unfortunately, the plugin, although functional, has not been updated for a long time. You can download it on the official website.
VPN
Speaking about privacy and anonymity on the Internet, you cannot ignore the use of VPN (with kill switch feature) for these purposes.
Having said that, you should NEVER use a VPN directly for carding or doing any cyber related activities because VPN is just a shield to protect your IP, you should always use an appropriate SOCKS5 to match your IP to carry out your tasks.
As you see all the necessary theory in our articles. However, we would like to remind you once again that VPN is not a magic-bullet.
Firstly, there are situations when traffic can “leak” past the VPN connection, and secondly, in networks based on the PPTP protocol, there is a real opportunity to decrypt the intercepted data (“Such an insecure VPN”). So you shouldn’t believe in complete security when using VPNs.
SUMMING UP
These are just the most popular solutions that allow you to somehow protect your privacy from the prying eyes of Big Brother.
Perhaps, in the near future, new technologies will appear, or we will all actively use one of the ones discussed today.
Who knows. Whatever it is, it is important to always remember that no solution can ever give a 100% guarantee of security.
Therefore, do not feel completely safe by installing Tor, I2P or something else – many have already paid for the feeling of false security.
That’s it! We are always here to support you by giving you access to our arsenal of tools and services that are we have available at your disposal at any given time.










Leave a Reply